 On the morning of Tuesday June 27 th, employees coming in to work at the offices of DLA Piper, one of the world’s largest law firms, were met with an unusual surprise. A whiteboard had been rolled out into the middle of the building lobby with “Attention: DLA Employees” written on it.
On the morning of Tuesday June 27 th, employees coming in to work at the offices of DLA Piper, one of the world’s largest law firms, were met with an unusual surprise. A whiteboard had been rolled out into the middle of the building lobby with “Attention: DLA Employees” written on it.
“All network services are down, DO NOT turn on your computers!” said the message. “Please remove all laptops from docking stations & keep turned off. No exceptions.”
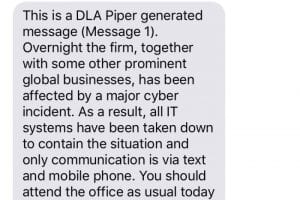
Text message notifications were urgently being sent out alerting the rest of the firm’s employees not to start their computers or connect to the DLA network. The phone system was down. So was email and the firm’s web portal. Without access to communications or documents, operations ground to a dramatic halt.
It soon became known that the firm had been infected by Petya Malware. As a result, the entire firm consisting of around 3,600 staff in over 40 countries, were completely locked out of the firm’s IT and communications systems.
What did this tech blackout actually mean to DLA ?
 “Consider litigators unable to access motions on a deadline. Trial lawyers preparing for arguments without key documents. Transactional lawyers unable to communicate with clients attempting to close multibillion-dollar deals.”- Roy Strom, The AM Law Daily
“Consider litigators unable to access motions on a deadline. Trial lawyers preparing for arguments without key documents. Transactional lawyers unable to communicate with clients attempting to close multibillion-dollar deals.”- Roy Strom, The AM Law Daily
It was to be a nightmare costing millions of dollars. What no one at DLA Piper knew or anticipated on that chaotic first day of the outbreak was that the lockdown wouldn’t be fully remediated for weeks to come.
A full day without phones, six days without email, nearly two weeks without complete access to older email and other documents. According to insurance brokers, the total direct and indirect costs associated with the attack on DLA Piper are in the millions. Ironically, the ransom demand for the cyber-attack was $300 in Bitcoin.
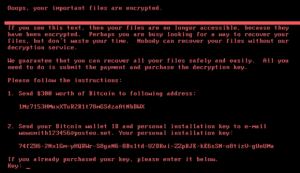 So why didn’t DLA Piper just pay the $300? Well obviously nobody should have a policy of paying criminals a ransom. However it turned out that they didn’t have the option to get the files back anyway as the “ransomware” involved in the attack wasn’t actually designed to make file recovery possible at all. This ransomware attack was designed purely to cause destruction – not to extort money.
So why didn’t DLA Piper just pay the $300? Well obviously nobody should have a policy of paying criminals a ransom. However it turned out that they didn’t have the option to get the files back anyway as the “ransomware” involved in the attack wasn’t actually designed to make file recovery possible at all. This ransomware attack was designed purely to cause destruction – not to extort money.
Therefore there was only one option – containment of the virus and restoration of infected systems. Two weeks after the initial infection DLA Piper confirmed that email and other tools central to client services had been brought safely back online, however other major systems were still being restored. To date that status doesn’t appear to have changed.
What lessons can you learn from this?
Cyber security awareness training and employing the right tech to secure your systems is obviously essential. However the importance of having a Business Continuity Plan that is regularly tested cannot be overstated. I don’t know how well DLA’s business continuity plan stood up in this incident, but there is one thing I can tell you for sure –
There are lots of businesses in the UK that are staggeringly under prepared and currently risk losing a lot of money. In fact some recent estimates have suggested that up to 70% of UK businesses are not capable of recovering after a serious incident without considerable damage to their business.
Therefore your Board, Senior Management, Operations and IT all need to have input when creating a business continuity plan.
As a starting point, here are my top 10 tips on how you can improve your business continuity.
If you want to learn more about Business Continuity Planning and how to create a plan that will keep your business operating, our workshops will help show you how. Register now.








