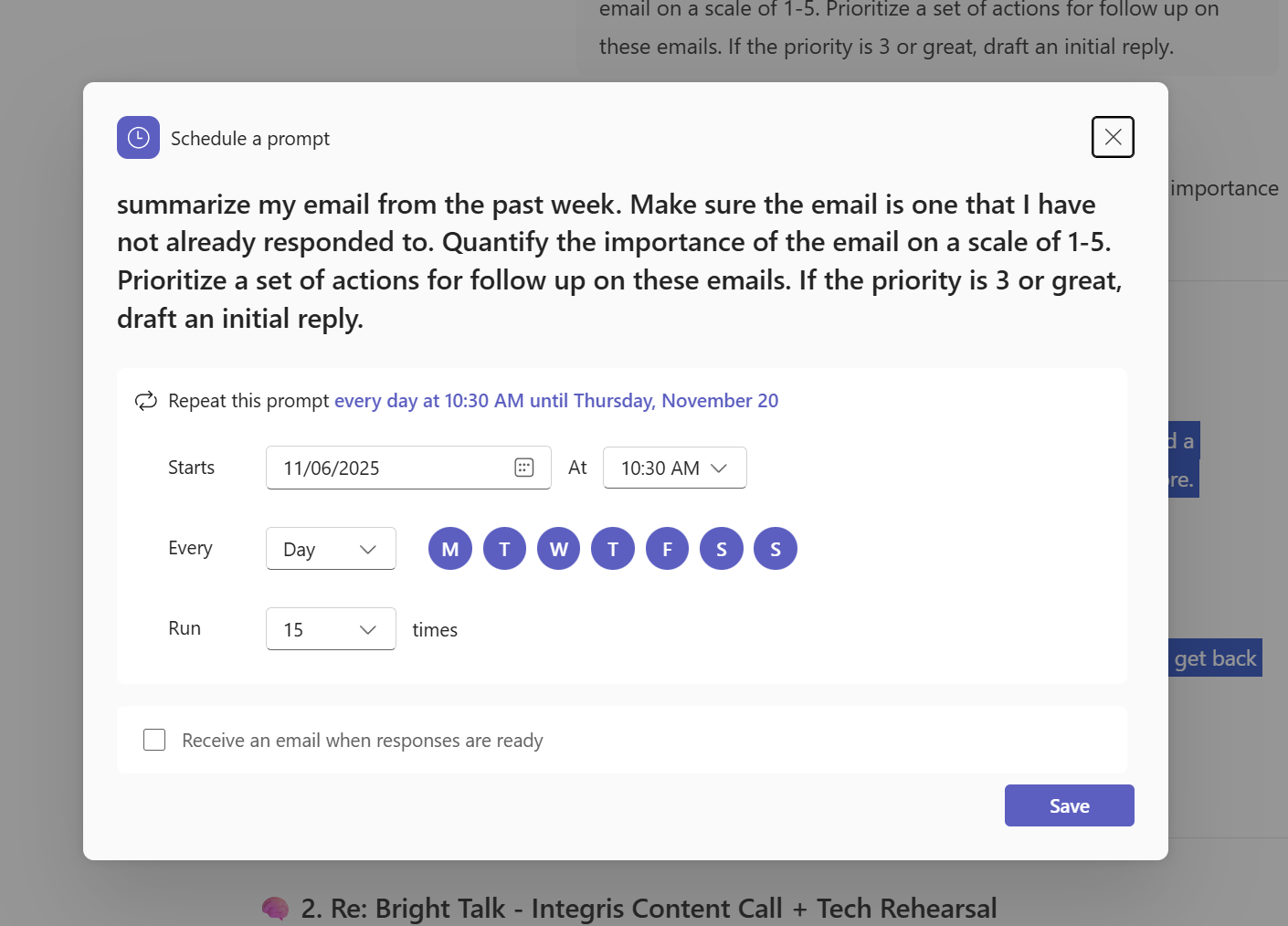
How Microsoft Copilot Turns Outlook into Your Executive Assistant
Opening your inbox first thing in the morning can feel overwhelming. Meeting invites, follow-up requests, and “quick questions” pile up before you’ve even started your day. It’s easy to lose hours reacting to emails instead of focusing on strategic work. Now imagine having an assistant who organises your schedule, prioritises what matters, and drafts [...]